Sep 27, 2012
Stand-Alone EM4x RFID Harvester
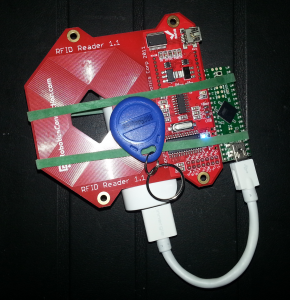
Continuing off from our last RFID Cloning with Proxmark3 post, we wanted to build a small, portable, stand-alone EM4x RFID tag stealer. We needed an easy way of storing multiple tag IDs whilst “rubbing elbows” with company personnel. The proxmark3 seemed liked an overkill and not particularly fast at reading em4x tags so we figured we’d try hooking up our RoboticsConnection RFID reader to a Teensy and see if we could make them play nicely together.
Continuing off from our last RFID Cloning with Proxmark3 post, we wanted to build a small, portable, stand-alone EM4x RFID tag stealer. We needed an easy way of storing multiple tag IDs whilst “rubbing elbows” with company personnel. The proxmark3 seemed liked an overkill and not particularly fast at reading em4x tags so we figured we’d try hooking up our RoboticsConnection RFID reader to a Teensy and see if we could make them play nicely together.
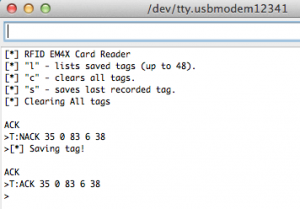
Hooking up the RFID reader to the Teensy was mostly painless. We connected the serial RX/TX pins on the reader to serial pins 2 and 3 on a Teensy 2++ and after a bit of mucking around, we got the RFID reader to respond to the serial commands sent from the Teensy. We re-implemeted a couple of basic reader commands in the Teensy, namely, “clear all tags“, “save last seen tag“, and “list tags“. This particular reader is also able to store up to 48 tags internally, simplifying our “data storage” issues significantly.
Our Teensy continuously monitors it’s serial input for new tags read by the RFID reader, and when one is found, it is automatically saved into the reader and an indication for this, the built in LED turns blue.
Once our “harvesting” session is complete, we can either use the Teensy to list all discovered tags, or connect to the RFID reader directly over USB. The tags are stored in non volatile memory on the reader, so it can be powered off safely.
You can download our demo Teensy sketch via GitHub:
[cc lang=”bash”]
git clone https://github.com/offensive-security/rfid-em4x-harvester
[/cc]
Stay in the know: Become an OffSec Insider
Get the latest updates about resources, events & promotions from OffSec!
Latest from OffSec

Research & Tutorials
CVE-2024-12029 – InvokeAI Deserialization of Untrusted Data vulnerability
CVE-2024-12029: A critical deserialization vulnerability in InvokeAI’s /api/v2/models/install endpoint allows remote code execution via malicious model files. Exploit risk for AI art servers.
Jul 17, 2025
0
Research & Tutorials
What is Phishing? Introduction to Phishing Demo (for Beginners)
Learn how phishing attacks work and how to spot them. Watch OffSec’s animated video to protect yourself from scams, spoofed sites, and social engineering.
Jul 15, 2025
2 min read

Research & Tutorials
CVE-2025-27636 – Remote Code Execution in Apache Camel via Case-Sensitive Header Filtering Bypass
Discover the critical Apache Camel vulnerability (CVE-2025-27636) that allows remote code execution via case-sensitive HTTP header manipulation in the exec component. Learn how attackers exploit this flaw and how to mitigate it.
Jul 10, 2025
2 min read