Nov 26, 2018
Exploit Database Redesign
Offensive Security is delighted to announce the complete redesign of The Exploit Database (EDB), making it easier and faster than ever to find the data you need and presenting it to you in a responsive dashboard layout.
Offensive Security is delighted to announce the complete redesign of The Exploit Database (EDB), making it easier and faster than ever to find the data you need and presenting it to you in a responsive dashboard layout.
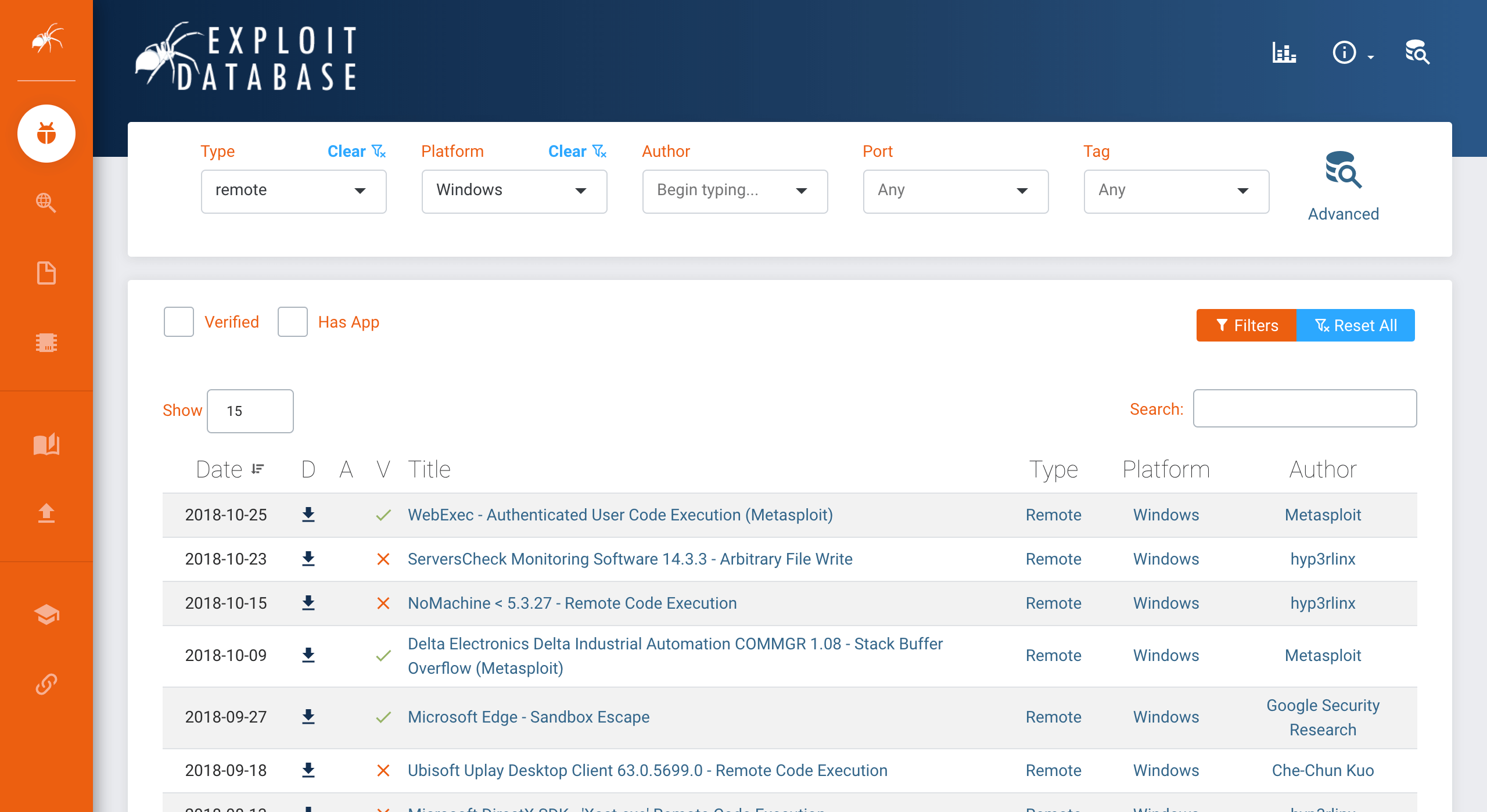
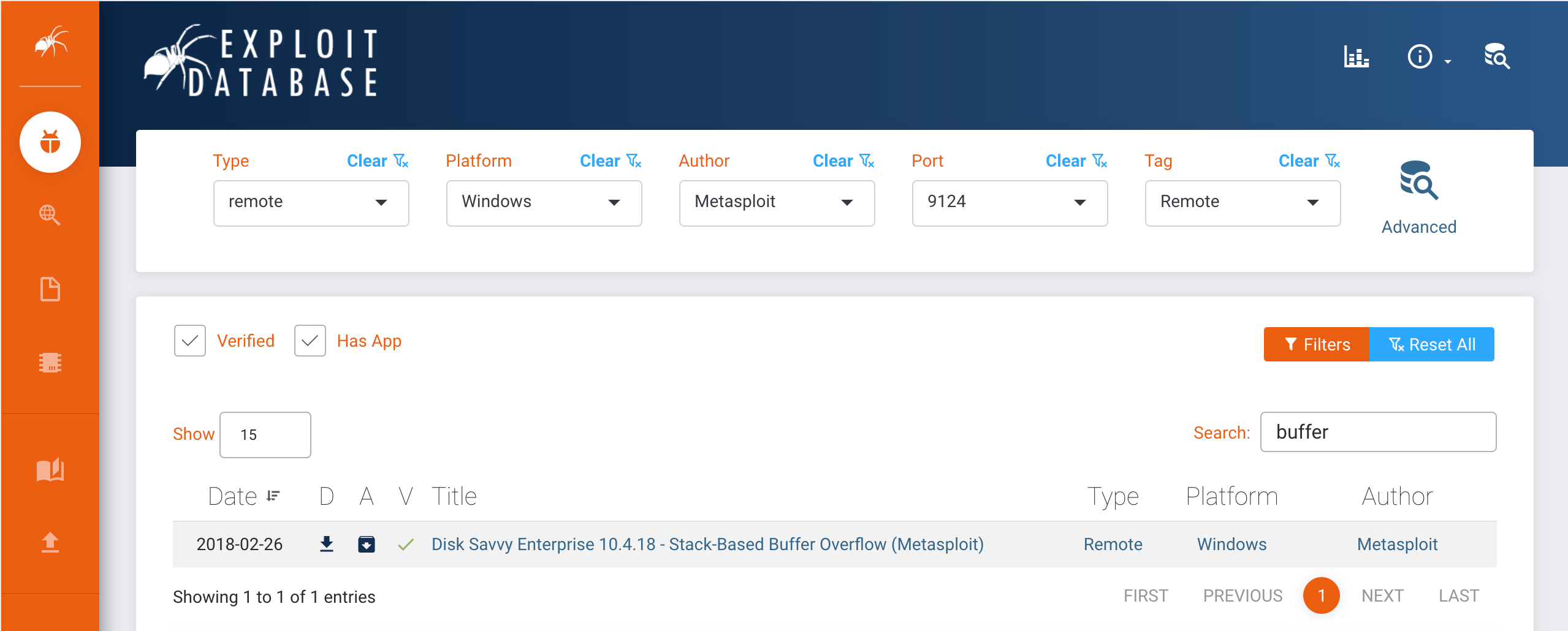
The update to EDB includes a complete redesign to improve the speed and accuracy of searches. This includes an all-new user interface, making it easier for testers and researchers to access the data they want, when they want it. For example, in the new version of EDB, it only takes two clicks to search and filter for remote exploits targeting the Windows platform. Prior to the redesign, this took at least five clicks to accomplish, depending on your familiarity with the site.
Some key elements of the update include:
- Instant searching of displayed results
- A new dashboard interface that helps users quickly see and do more with the database
- Dynamic filters that enable quick switching between types, platforms, authors, ports and tags
- Clearly defined sections for exploits, papers, shellcode and the Google Hacking Database (GHDB), with a common look and feel throughout
- Ability to quickly limit results to those that have been verified and those for which we have hosted a copy of the vulnerable application
We hope you love this redesign as much as we do but if you really can’t stand it, the old interface is available (for now) at old.exploit-db.com. All of these new features are just the beginning. Over the next few months, we will be continuing to add new features to the platform so stay tuned for more information.
Stay in the know: Become an OffSec Insider
Get the latest updates about resources, events & promotions from OffSec!
Latest from OffSec

Research & Tutorials
CVE-2025-27636 – Remote Code Execution in Apache Camel via Case-Sensitive Header Filtering Bypass
Discover the critical Apache Camel vulnerability (CVE-2025-27636) that allows remote code execution via case-sensitive HTTP header manipulation in the exec component. Learn how attackers exploit this flaw and how to mitigate it.
Jul 10, 2025
2 min read

Research & Tutorials
CVE-2025-29306 – Unauthenticated Remote Code Execution in FoxCMS v1.2.5 via Unserialize Injection
Discover details about CVE-2025-29306, a critical RCE vulnerability in FoxCMS 1.2.5. Learn how unsafe use of PHP’s unserialize() function enables remote attackers to execute arbitrary system commands.
Jul 3, 2025
2 min read

Research & Tutorials
CVE-2024-39914 – Unauthenticated Command Injection in FOG Project’s export.php
Discover details about CVE-2024-39914, a critical unauthenticated command injection vulnerability in FOG Project ≤ 1.5.10.34. Learn how attackers can exploit export.php to execute system commands or deploy persistent webshells.
Jun 26, 2025
2 min read